Data-driven Product Authenticity Using Machine Learning
The problem of counterfeit goods in the consumer products industry continues to grow unchecked, with 2018 bringing revenue losses of $1.2 trillion*. It is abundantly clear that current anti-counterfeit measures aren’t able to address this hugely damaging trend. At EVRYTHNG we’ve been busy developing a brand protection solution which harnesses the power of machine learning to finally give brands the weapons they need to win the fight.
We are proud to introduce a new, Web-native way to authenticate products. It doesn’t require dedicated software, proprietary tags or changes to manufacturing processes. We leverage state-of-the-art machine learning technologies and a user-centric product authenticity toolkit to examine both physical and digital characteristics of a product to determine its authenticity.
Data-Driven Product Authenticity by Hand
The best way to understand how data-driven product authenticity using machine learning works is to conduct a simple test of how it would work without machine learning in the EVRYTHNG platform, that is how it would work if you were manually checking the authenticity of a product.
- Step One: Purchase or find a recently purchased piece of clothing in your closet. Ask yourself this question—Is the brand authentic? How can I be sure?
- Step Two: Examine the label. Is it intact? Have you seen this type of label before? Examine the label more carefully. Does it look genuine? Is it written in the local language, containing the usual instructions and warnings?
- Step Three: If you’re satisfied the label is genuine, examine the clothing. For example, look at the stitches. Are they properly aligned?
- Step Four: Don’t put your garment away just yet. Examining the physical product can only take you so far. Counterfeiters can tamper with the physical product, they can make near-perfect copies or produce backdoor goods. Parallel importers can circumvent local regulators by reselling products originally destined for another market. But… one thing they can’t do is re-create or modify the product-related data stored online by consumers, retailers and manufacturers.
- Step Five: Information is power, so let’s use this to our advantage. We want to find out if others in your region bought the same garment. Take a picture of the clothing and do an image search. Are you getting results that match your garment? Also take a close look at the barcode number or item number on the label. Does it match the barcodes on the clothes you are finding online? Does the search result return online shops in your area that sell this product?
You’ve just manually completed your first data-driven product authentication! And all this using off-the-shelf software and without using any proprietary tags or markers, simply by using the power of various available data sources. The combination of multiple authentication factors provides assurance the garment you purchased is genuine, even if in isolation each data point is insufficient, when combined, we have a very powerful indicator of authenticity.
Now let us explain how we automated this process with machine learning in the EVRYTHNG platform.

So How Does It Work?
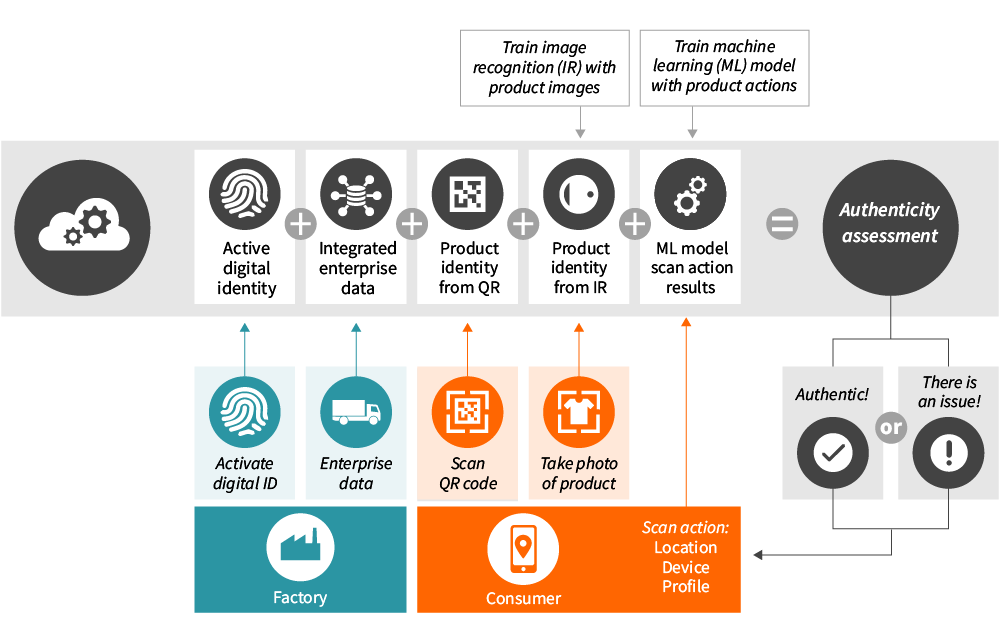
If the garment has a QR code with GS1 Digital Link (the GS1 Standard co-chaired by EVRYTHNG’s co-founder and CTO Dominique Guinard) and an Active Digital Identity in the cloud managed by EVRYTHNG, consumers can very simply access the data-driven product authenticity Web app by scanning the garment’s QR code with a mobile phone. The Web app will ask the consumer to take a picture of the garment and submit it to the app. A few seconds later, the app provides notification of authenticity. It’s really that simple!
Diving Deeper into the Technology
The unique item-level identity forms the backbone of data-driven product authenticity. The GS1 Digital Link is a standard product URL that can be decoded by industrial scanners as well as ordinary smartphones. Brands using the EVRYTHNG platform to manage products can produce items #borndigital. Each individual product item comes with a GS1 Digital Link encoded in a QR or NFC tag and an Active Digital Identity in the cloud. This is a key advantage of the EVRYTHNG platform. The fact that most smartphones either come equipped with native QR code reading capabilities (e.g. the iOS Camera app) or a widely adopted app which can read QR codes (e.g. Twitter, WeChat, etc.) installed, means brands can anticipate a large adoption rate. With the EVRYTHNG data-driven product authenticity app, consumers simply scan the QR code on the item they would like to authenticate.
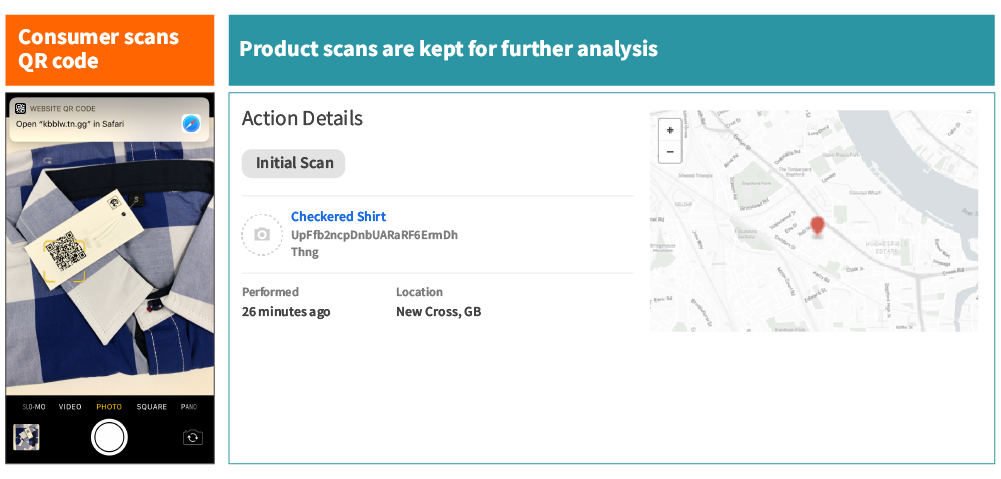
Scan Mapping
Information is stored in the EVRYTHNG Platform every time a product QR code is stored. Over time, this creates a map of related scans including, frequency and context—for instance, the location, market segment, or time of day in which the scans occurred. Using unsupervised machine learning techniques such as, isolation forests for anomaly detection, penalises product scans that differ too much from scans of related products. This is useful information because parallel imports, backdoor goods or counterfeit products would reflect this lower score, since products are being scanned in the wrong location and in the wrong context.
Creating a Digital History
Next, we consider an individual product’s digital history. Each item has actions, or events created through steps in the manufacturing and supply chain. For example, a manufacturer scans the item, or internal attributes of the item like, temperature resulting in an action. EVRYTHNG’s rule-engine “Reactor” automates business rules for these actions. For example, an item must first be scanned by its manufacturer to be activated. A product that has not been activated by the manufacturer will result in a very low authenticity score, because it is likely to be a counterfeit.
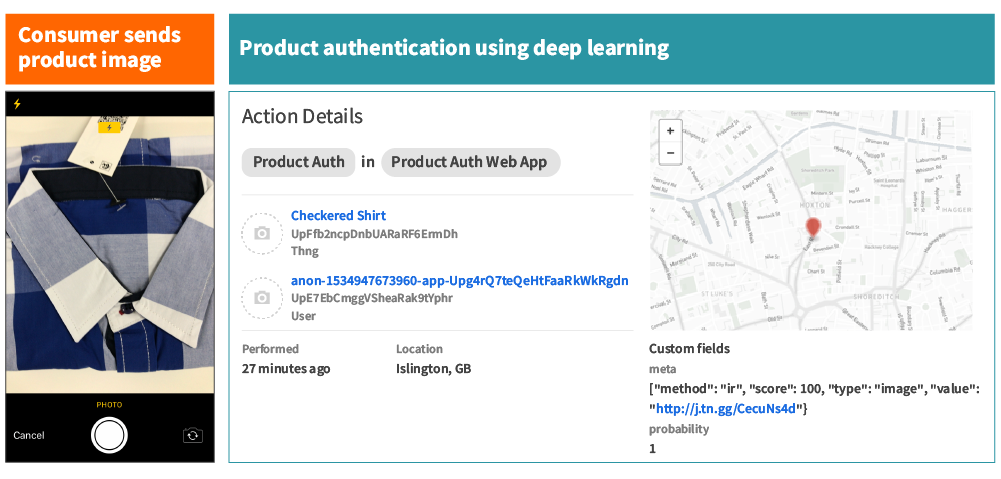
Product Authentication
Finally, we also want to authenticate the physical product. Conceptually, the fingerprint of the item you have in your hands is compared to the reference fingerprint of its product type. The closer they match, the more likely the product is genuine. It is important to mention that each product item has a unique code. By scanning the QR code, not only do we know it is the correct item but also its product type.
How does physical authentication work on the EVRYTHNG platform? We developed a computer vision component that allows brands to train a convolutional neural network with authentic product images. The model learns to classify images of products based on different visual characteristics, such as color, stitches, texture, or label placement. When a consumer submits an image, the model classifies the image and returns the product ID and prediction probability. The higher the probability, the higher the overall authentication score. If the model returns the wrong product ID with a high probability, we can expect a counterfeit product.
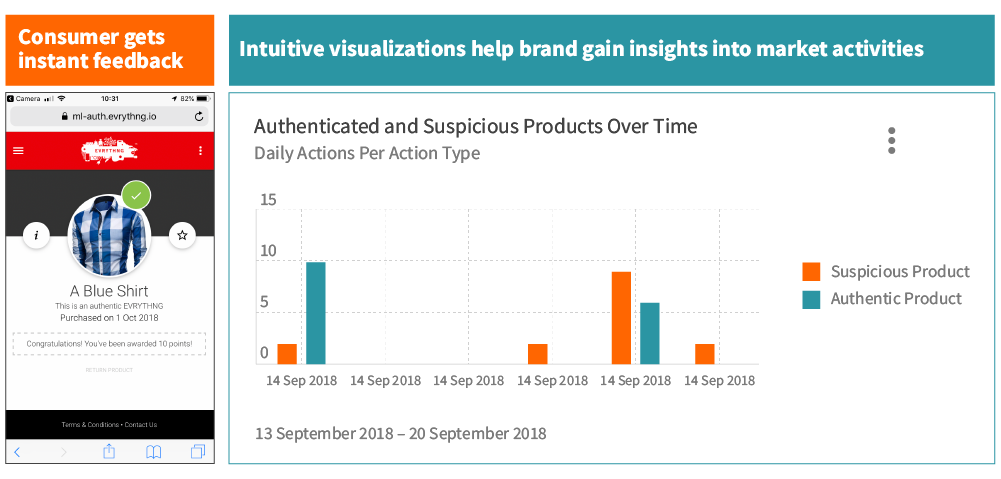
The final step is to inform consumers whether the product they purchased is authentic. For brands, each time a consumer registers a product to verify authenticity, they receive valuable lifecycle insights and alerts to help analyse and react to gray market and counterfeit behaviour.
By using the EVRYTHNG platform and our new machine learning tools, brands can leverage data to directly engage with consumers while combating counterfeit and gray market imports. EVRYTHNG calculates the probability that a product is authentic by combining multiple factors from the digital supply chain. Authentication factors include: checkpoints along the supply chain, product profile data and anonymised feedback from users who bought similar products. With patent pending technology in this field, EVRYTHNG provides consumer product brands with the tools to leverage powerful real-time data in their digital supply chain, while empowering consumers by giving them the tools to make informed decisions about the products they buy.
(*Source: Global Brand Counterfeiting Report, 2018 – R Strategic Global 2018)
(Shared from the EVRYTHNG website, originally published Jan. 28, 2019)
